1 Introduction
Privileged Access Management (PAM) solutions are critical cybersecurity controls that address the security risks associated with the use of privileged access in organizations and companies. Traditionally, there have been primarily two types of privileged users:
-
Privileged IT Users – those who need access to IT infrastructure and applications supporting the business for cloud and on-premises workloads. Such permissions are usually granted to IT admins who need access to system accounts, software accounts or operational accounts.
-
Privileged Business Users - those who need access to sensitive data and information assets such as HR records, payroll details, financial information or intellectual property, and social media accounts but work outside the IT organization.
In recent years the picture has become more complicated with many more non-traditional users requiring and getting privileged access to IT and business data. Some will be employees working on special projects, others may be developers building applications or third-party contractual workers.
In recent years, PAM solutions have become more sophisticated making them robust security management tools in themselves. While credential vaulting, password rotation, controlled elevation and delegation of privileges, session establishment and activity monitoring are now almost standard features, more advanced capabilities such as managing credentials for non-human users, replacing scripts and dynamic secrets, offering native access to end users and the ability to embrace PAM scenarios in an enterprise governance program are becoming the new standard to protect against today’s threats - all integrated into comprehensive PAM suites. PAM is also available as-a-service from a number of vendors with much of the core functionality hosted outside the organization in the cloud.
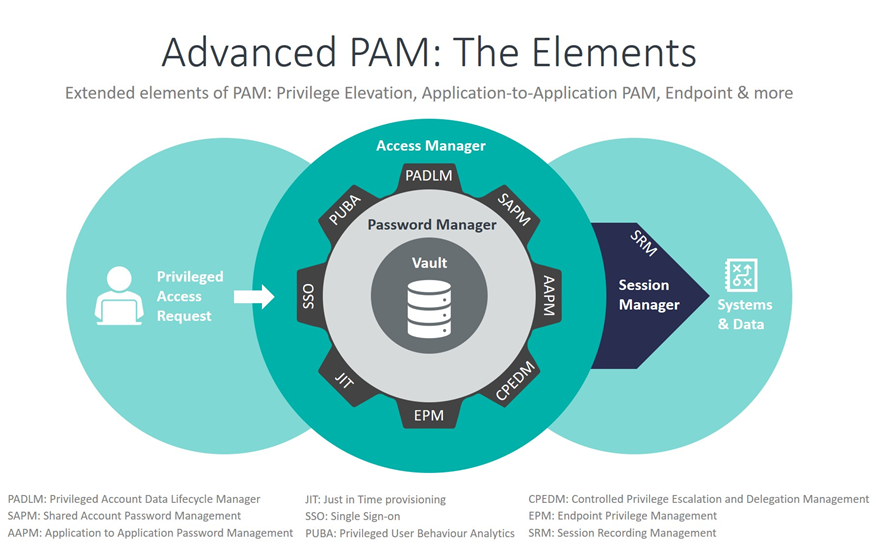
PADLM: Privileged Account Data Lifecycle Manager
SAPM: Shared Account Password Management
AAPM: Application to Application Password Management
CPEDM: Controlled Privilege Escalation and Delegation Management
EPM: Endpoint Privilege Management
SRM: Session Recording Management
JIT: Just in Time provisioning
SSO: Single Sign-on
PUBA: Privileged User Behavior Analytics
Among the key challenges that drive the need for privilege management are:
- Abuse of shared credentials;
- Abuse of elevated privileges by unauthorized users;
- Hijacking of privileged credentials by cyber-criminals;
- Abuse of privileges on third-party systems;
- Accidental misuse of elevated privileges by users.
- The requirement to perform attestations on privileged users and admin accounts
Furthermore, there are several other operational, governance and regulatory requirements associated with privileged access:
- Discovery of shared accounts, software and service accounts across the IT infrastructure;
- Identifying and tracking of ownership of privileged accounts throughout their lifecycle;
- Establishing Single Sign-on and/or native secure sessions to target systems for better operational efficiency of administrators;
- Auditing, recording and monitoring of privileged activities for regulatory compliance;
- Managing, restricting, and monitoring administrative access of IT outsourcing vendors and MSPs (Managed Service Providers) to internal IT systems;
- Managing, restricting, and monitoring administrative access of internal users to cloud services.




































