What Is Identity & Access Management?
Identity & Access Management (IAM) is one of today’s core disciplines of IT (Information Technology), and an essential element within every cybersecurity strategy. However, IAM is not limited to security, but is also one of the enablers of digital transformation.
IAM Core Technologies: IGA, Access Management, PAM
Dealing with customers, consumers, or connected things is about dealing with their digital identities. It is about IAM. IAM, sometimes abbreviated to Identity Management, is easy to describe: It is everything that helps in managing identities and their access. It is about the “who” and the “what”: Who can do what in IT? Who can log on? Who can access which data?
IAM consists of a wide range of technologies. However, there are three technologies at the core:
- User Lifecycle Management & Access Governance
- Access Management & Federation
- Privileged Access Management
While these areas form the foundation of IAM, there are more elements in IAM such as directory services as sort of a database of all the users, and Identity Verification for the first-time proof of an identity during the onboarding process, e.g., by comparing the face via video with the photo on the person’s passport.
Traditional IAM Architecture: What Is the Foundation of IAM?
The first core area of IAM, User Lifecycle Management & Access Governance, is also referred to as IGA (Identity Governance & Administration). User Lifecycle Management is also called Identity Provisioning. But what are all these terms about? Essentially, there are two parts: the management of the user’s lifecycle, and the governance of access.
The Foundation: User Lifecycle Management & Identity Provisioning
User Lifecycle Management is about the entire identity management process from creating a digital identity when onboarding a person such as a new employee, to retiring that digital identity. It involves creating user accounts in systems and managing changes, e.g., when someone moves to another department. These processes are commonly referred to as JML (joiner, mover & leaver) processes. User Lifecycle Management supports and automates such processes.
The other part of User Lifecycle Management & Access Governance is about requesting, approving, and reviewing access entitlements. It is about who should have access to which systems, applications, and data. Automated and manual requests for data must be supported, including access request and approval workflows. Access reviews are required for regulatory compliance, to check regularly whether the access is still needed or must be revoked.
User Lifecycle Management is tightly coupled with Identity Provisioning. While User Lifecycle Management looks at the JML processes and other parts of the lifecycle, Identity Provisioning is about technically connecting IGA with the target systems such as Microsoft Active Directory or SAP, for e.g., creating user accounts, and assigning entitlements.
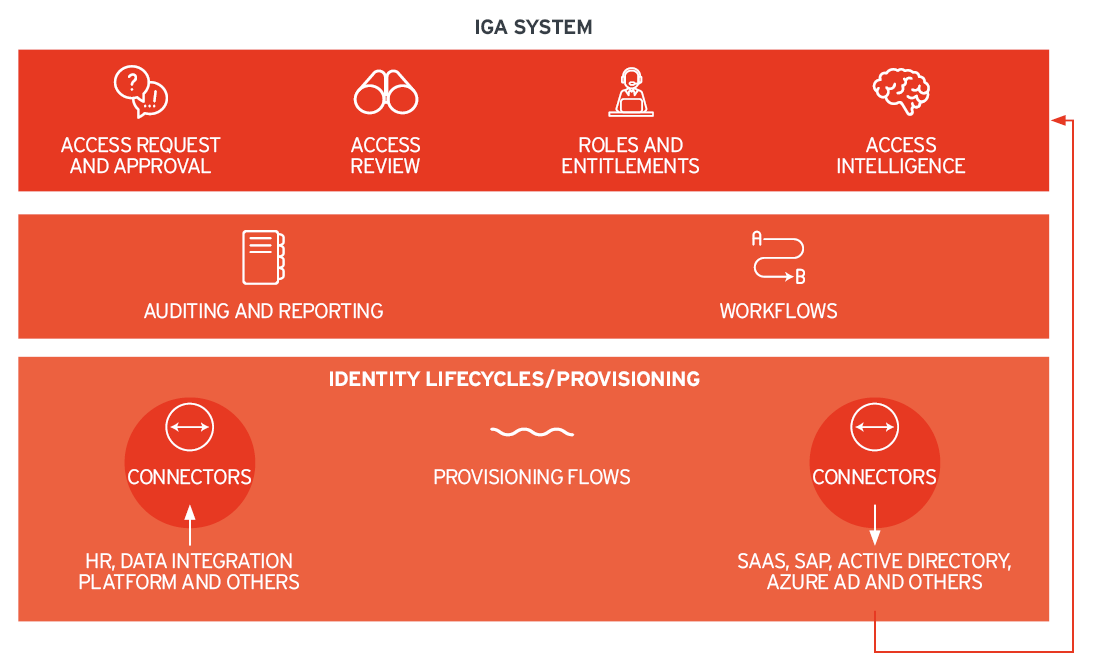
Authentication and More: Access Management & Identity Federation
The second major discipline of IAM, Access Management & Federation or just Access Management, is about access to systems at runtime. After a user has an account, that user will log on.
.png)
That requires authentication, i.e. the verification that credentials such as user name and password have been entered correctly. Access Management also includes federation to other systems, a concept where for instance a user is authenticated in his organization and then logs on to the organization’s tenant of a SaaS (Software as a Service) application such as Salesforce. In that case, Salesforce trusts the organization to manage authentication correctly, and federates the users from that organization to the respective tenant in Salesforce. Access federation is based on established standards such as OAuth2, SAML (Security Assertion Markup Language), and OIDC (OpenID Connect).
Protecting Most Critical Access: Privileged Access Management
Last not least, there is PAM or Privileged Access Management, which is a most technical discipline of IAM that deals with the specifics of highly privileged users such as administrators logging into systems, e.g., as Windows administrator or root user on Linux.
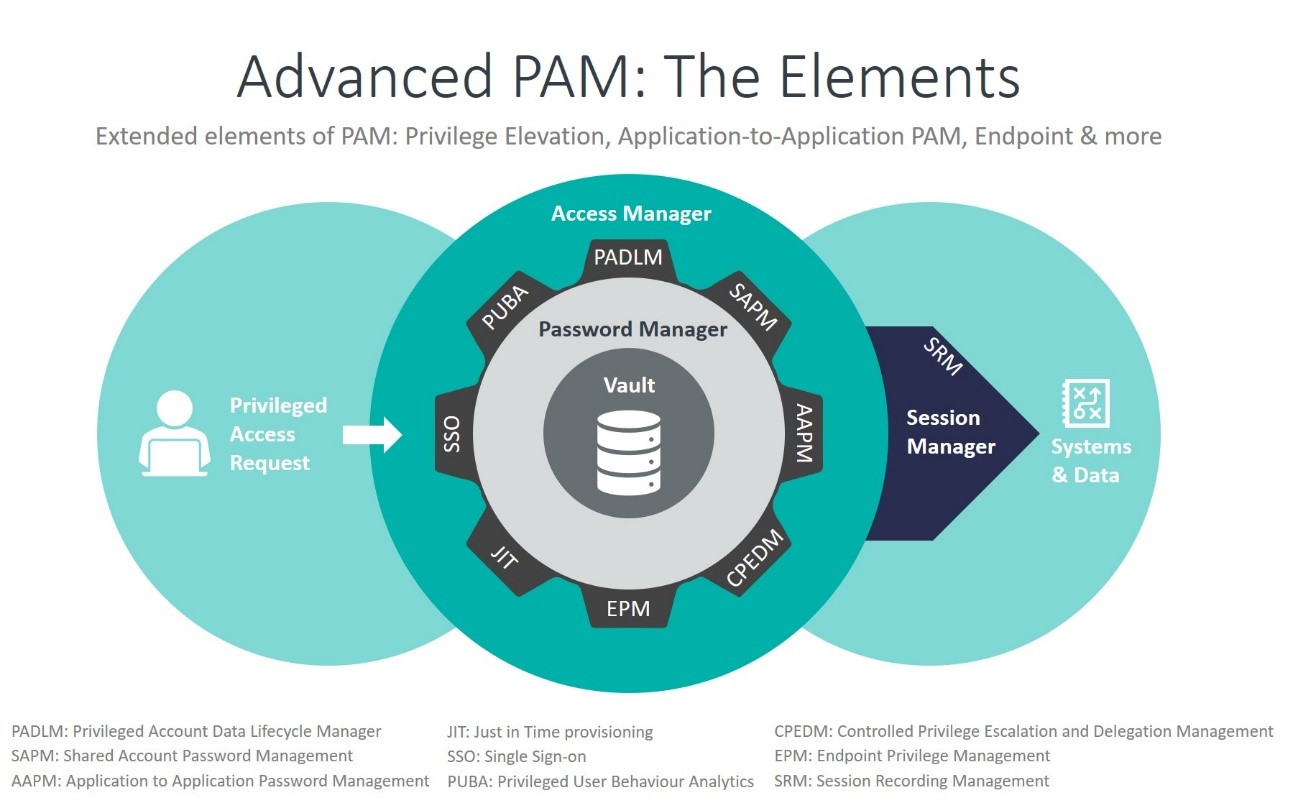
Some of the aspects covered by PAM solutions are rotating passwords for shared accounts, and session management. Shared accounts such as root can be used by multiple persons. To mitigate the risks, users of privileged accounts must not use the same password. PAM ensures (amongst many other features) that privileged account users always get a new password for each new access. The session management part of PAM is about recording sessions, e.g., for forensics, and for logging and monitoring what happens during privileged access.
Understanding the Downside of Legacy IAM
Traditionally, these three groups of capabilities have been deployed on-premises, with specialized tools for each of the areas. Most organizations started with User Lifecycle Management & Access Governance, and Access Management, adding Privileged Access Management later.
The Tough Part of IAM: Connecting to the Managed IT Systems
Creating user accounts in a range of systems such as Microsoft Active Directory, Microsoft Azure Active Directory, LDAP servers, on email servers, mainframes, business applications such as SAP, specialized banking apps, new SaaS services, and many more requires technical integration with these systems via connectors. That part of integration is challenging, despite SCIM (System for Cross-domain Identity Management) becoming increasingly established as a standard.
Standards Evolving: SaaS Is Easier to Manage
With the shift of workloads to SaaS services, SCIM for User Lifecycle Management and other standards such as OAuth and OIDC for authentication are becoming the norm, simplifying integration. For Access Management & Federation, this is already the norm. For the other areas, there is also a tendency towards IDaaS (Identity as a Service), even while the maturity of solutions is still is lower than for Access Management.
The Benefits of Modern IAM Platforms
Modern IAM platforms deliver various benefits. The obvious one is that they are deployed using as-a-service models, avoiding the complex installation and operation of IAM on-premises. However, integration with legacy backends such as mainframes still requires setting up connectors..
The Need for Flexibility: Pure On-Premises IAM Is Not Sufficient Anymore
Most, but not all, IDaaS offerings in the market are available in both pure SaaS deployments and other options, enabling, e.g., hybrid deployments or a simplified migration from on-premises to the cloud. Modern architectures, based on microservices and building on container-based deployments, give the customer much more flexibility in deployment than traditional models.
Updates and patches in SaaS are managed by the providers, simplifying operations and allowing the customers to concentrate on the user-focused and business-focused aspects of IAM, instead of technology, such as building efficient workflows and managing user access.
The Role of Microservices and APIs in IAM
Furthermore, customization is simplified in modern architectures, because customizations can be well-segregated from the IAM service into separate microservices. This also is due to the fact that modern IAM comes with a comprehensive set of APIs (Application Programming Interfaces), which expose the capabilities of the IAM products and can be utilized in customization.
The Identity Fabric: A Paradigm for Modern IAM
IAM, over the years, evolved – and became increasingly complex. Aside from the major disciplines, many specialized solutions appeared and, sometimes, disappeared again. With IAM starting to support other groups of users such as customers, new disciplines such as CIAM (Consumer/Customer IAM) evolved.
Unifying IAM: Managing Access of Everyone and Everything to Every Service
The paradigm of the Identity Fabric, defined by KuppingerCole Analysts, provides model for a unified approach to IAM. It starts with looking at what IAM is for: The task of IAM is enabling seamless, controlled, and secure access of everyone and everything to every service. Not more, not less.
The Identity Fabric is based on analyzing the major capabilities required by an organization, which should be done based on the use cases (such as managing access of consumers to an ecommerce system) and the required technical capabilities. The latter can be, e.g., based on a Reference Architecture. These capabilities are grouped into services that are delivered by technology. Ideally, that technology is provided in modern architectures, i.e., container-based deployments and based on microservices, providing a comprehensive set of APIs.
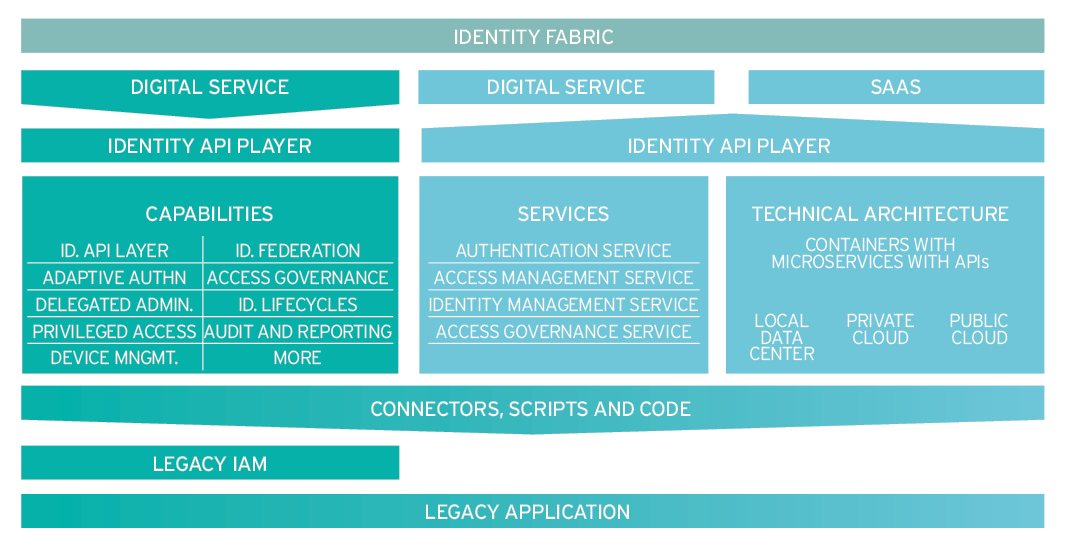
Identity Fabrics: Enabling Both Agility and Gradual Migration
Identity Fabrics support both legacy applications, and modern SaaS applications and digital services. They connect to existing solutions, either directly or by utilizing legacy IAM solutions. They also use standards such as SCIM and OIDC, but also specialized connectors, to connect to modern SaaS services.
Based on the broad set of APIs, they also enable modern digital services to request IAM services. Thus, a digital service, e.g., can use APIs for registering new users, instead of creating a user registration capability for each new digital service. Identity Fabrics help in moving from traditional IAM architectures towards modern architectures, but also in unifying different IAM initiatives across capability areas such as User Lifecycle Management and Access/Federation, or across identity types, such as Employee IAM and Customer IAM.
The IAM Reference Architecture
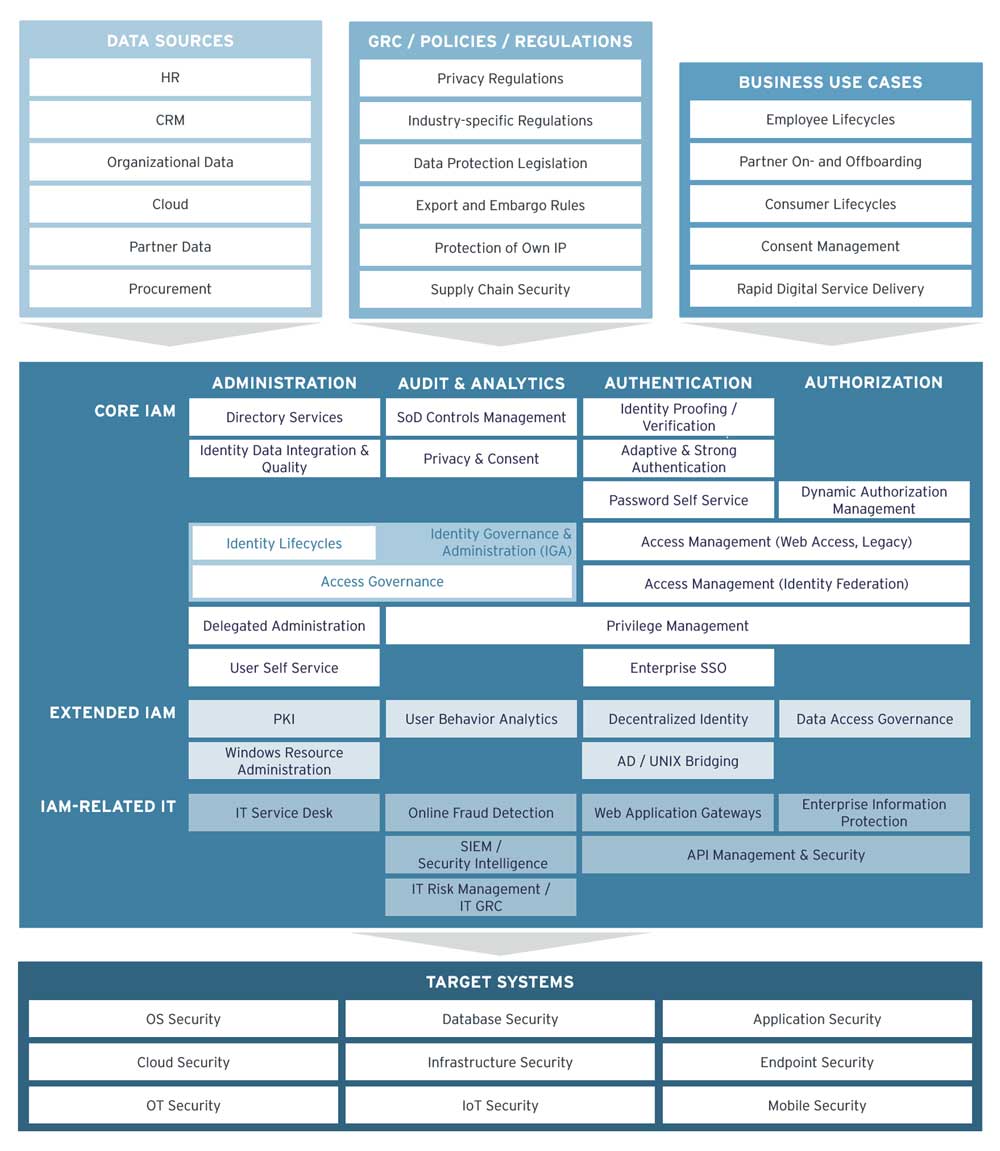
On a more technical level, there is the KuppingerCole IAM Reference Architecture, which describes the various components that make up IAM or are related to IAM. The Reference Architecture is split into four vertical columns and three horizontal layers. Let's dive right in.
Administration, Auditing, Authentication, and Authorization
The vertical columns are Administration, Auditing, Authentication, and Authorization – the four As of IAM.
- Administration: Managing digital identities, the user accounts, passwords, etc.
- Auditing: The governance capabilities such as access review or SoD (Segregation of Duties) controls.
- Authentication: Everything around authentication, from Identity Verification and risk- and context-based authentication to Identity Federation.
- Authorization: The authorization of access requests, e.g., by supporting requests from digital services to authorize users at runtime, the so-called Dynamic Authorization Management.
Anne Bailey and Matthias Reinwarth take on Verified Digital Identity in an episode of the Analyst Chat podcast. Listen in and explore what these are, why they are becoming increasingly important and where they add new aspects to the concept of digital identity. The horizontal layers are Core IAM, Extended IAM, and related areas.
The latter may be considered as part of IAM, or separate disciplines. As with every reference architecture, this is a blueprint that can be adjusted to specific requirements of an organization. It helps in identifying and prioritizing the relevant elements in an IAM and creating the roadmap towards the own IAM infrastructure.
IAM Vendors Overview
Even in the core IAM market, there is already more than 100 vendors. Looking at all the specialized disciplines, there are a hundreds of vendors. Let's take a look at the key players of each segment.
Key Players in IGA
Thus, identifying the right set of capabilities – e.g., by utilizing the IAM Reference Architecture – and defining a blueprint – e.g., based on the Identity Fabrics model – is the foundation to identify the capabilities and a reasonable set of technology providers for the IAM core capabilities and specialized further capabilities that are required. For User Lifecycle Management & Access Governance, the leading vendors (based on Overall Leadership in the relevant KuppingerCole Leadership Compasses) include, in alphabetical order, Broadcom, EmpowerID, Hitachi ID, IBM, Micro Focus, Microsoft, Okta, Omada, One Identity, Oracle, RSA, SailPoint, SAP, and Saviynt.
Key Players in Access Management
For Access Management & Federation, these are, again in alphabetical order, Broadcom, CyberArk, ForgeRock, IBM, Ilantus, Micro Focus, Microsoft, Okta, OneLogin, Oracle, Ping Identity, and RSA.
Key Players in Privileged Access Management
For Privileged Access Management, these are (in alphabetical order) BeyondTrust, Broadcom, Centrify, CyberArk, Hitachi ID, One Identity, SSH, Thycotic, and Wallix. However, as mentioned, there are many more vendors in these market segments as well as in the overall market. Our KuppingerCole Leadership Compass and Market Compass documents provide a comprehensive overview about the most relevant IAM vendors.
What to Consider When Choosing a Vendor
Selecting IAM vendors – as with every other vendor in IT – should always start with the requirements. What are the main use cases and what are the most relevant technical capabilities? Which areas should be prioritized?
Don’t Start With the Tool – Understand Your Requirements First
Based on the requirements, the relevant market segments must be identified. Don’t compare apples and oranges, but look for the right solutions for the right problem. Again, the KuppingerCole Leadership Compass and Market Compass documents as well as the Buyer’s Compass, list key requirements, criteria, and critical capabilities to provide guidance.
For the market segment, a longlist of vendors containing all vendors that may be a fit should be created. In a first round of evaluation, the four to six vendors that are the best fit from a high-level capability perspective, but also with respect to supported deployment models, should be selected. These are then included in the RfI (Request for Information) and RfP (Request for Proposal). The RfI looks in detail at functional and non-functional requirements, while the RfP adds the cost perspective. The RfI process also includes vendor presentation.
The Right Approach: Longlist, Shortlist, Proof of Concept
From the shortlisted vendors, commonly two are included in a subsequent PoC (Proof of Concept), where major use cases and capabilities are tested in practice, before making a final decision and moving to contract negotiations. When looking at this from a high-level perspective, it is most important to select vendors that support the full breadth of systems well, in modern architectures and deployments.
It is equally important to find a good balance between supporting all the specific requirements and a reasonably small set of providers to avoid ending up with a zoo of tools. Machine Learning systems are ideally suited to the tasks of systems management where there are clear rules and well-defined environments.
IAM Outlook: What Does the Future Hold for IAM?
IAM is under constant change. Cloud first strategies, IAM modernization, modern architecture models and agile IT are just some of the factors driving the evolution of IAM. Don’t stop with where you are on your IAM journey, but always look for what is next in IAM. IAM is constantly evolving. There are many new evolutions and trends in IAM. Three of the most important ones are:
- Identity of things, devices, and services: IAM is not only about humans. It is also about the identity of things (such as in IoT, the Internet of Things), of devices (such as mobile devices), and services (such as apps or software robots). IAM also is about the relationship between humans, things, and devices. Digital transformation use cases do not work without supporting all these devices and their relationships – just think about the different people owning and driving connected vehicles and controlling these with apps from their smartphones.
- Decentralized Identity: While identities traditionally have been managed by the applications, the reuse of identities, e.g., as a consumer dealing with many retailers, has become essential. With the concept of decentralized identities (DIDs), there is a new paradigm that supports this concept.
- Integration into other platforms: More and more identity capabilities are shifting into SaaS and IaaS platforms, including, e.g., ITSM/ESM (IT Service Management/Enterprise Service Management). This allows for a more seamless integration of processes. That integration brings both opportunities and challenges, with the risk of identity capabilities sprawling across too many places.
Again: There is continual innovation in IAM, which delivers new options for customers. Modern architectures such as the Identity Fabric help in preparing for IAM evolution, in contrast to the traditional, monolithic IAM tools running on-premises.
Bottom Line and Recommendations
Ready for a new, a better, a more modern IAM? Understand today’s and the future requirements, make a plan, define your own IAM and Identity Fabric and execute on it, for serving the Digital Transformation of your organization.
7 Steps Towards A Successful IAM Program
The seven steps are:
- Get your stakeholders on board
- Understand the requirements of business and IT
- Define a program, and gather the funding
- Define your blueprint & architecture – your vision of a future Identity Fabric that fits to your organization
- Build your IAM organization
- Select the technology & tools you need, based on your requirements, blueprint & architecture
- Execute in well-defined steps – the projects within your program
IAM is at the core of the digital transformation, at the core of cybersecurity, and at the core of regulatory compliance. It is essential, therefore, to have both a mature and a modern IAM in place. For many organizations, there is a need for IAM modernization, shifting from traditional approaches towards a modern IAM.
Both the models such as the KuppingerCole Identity Fabric, and the technology, as described in the KuppingerCole Leadership Compass and Market Compass documents, are available for building a modern IAM infrastructure.




































