What is Identity Governance and Administration?
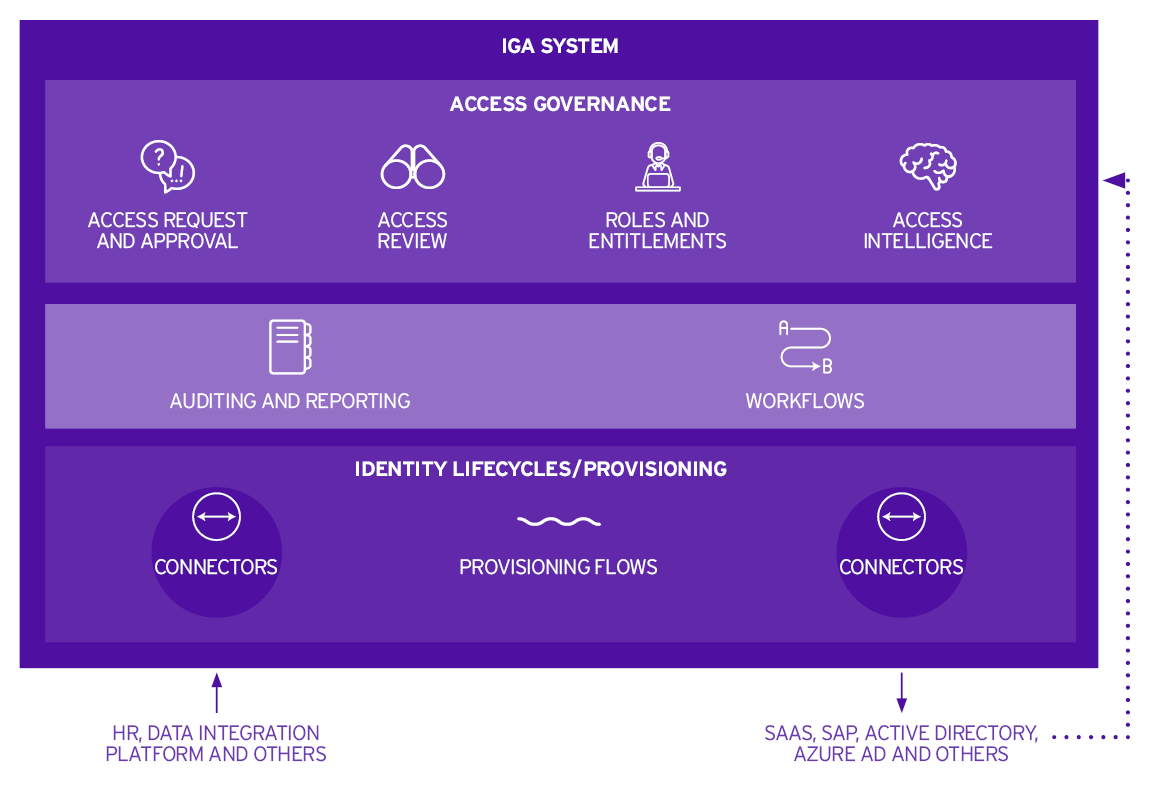
IGA is a core component of IAM infrastructure and refers to integrated solutions that combine Identity Lifecycle Management and Access Governance. IGA helps to cut costs, increase security, improve compliance, and give users access to the IT resources they need.
Access Governance
Access Governance is one of the two main elements of Identity Governance and Administration (IGA) that appeared initially as separate solutions before being integrated with Identity Provisioning in combined IGA solutions. Access Governance refers to the specific processes that are aimed at reducing risk by enforcing the principle of least privilege continually to prevent privilege creep as individuals’ roles change.
An important part of Access Governance is ensuring that as roles and responsibilities change, or when individuals leave an organization, their access rights are increased or revoked accordingly. Access Governance, therefore, is typically part of the standard joiner, mover, leaver processes. Access Governance also covers the key processes of access requests and approvals, access reviews, roles and entitlements, and access intelligence.
Access Governance has become increasingly important with the introduction of a growing number of data protection regulations that require organizations to keep a strict control on who has access to personally identifiable information (PII). The integration of Identity Provisioning and Access Governance in IGA solutions means these two areas now share a single UI, integrated auditing and reporting, workflows, and some connectors.
Identity Lifecycle Management
Identity Lifecycle Management or Identity Provisioning is the second main element of IGA that appeared before Access Governance solutions to handle all aspects of creating and managing access to IT resources to ensure all users have access to everything they need to do their jobs.
In the context of an integrated IGA solution, Identity Lifecycle Management is about integration with source and target systems. It is about delivering the technical flow of data using connectors from source systems such as HR and Data Integration Platforms to target systems such as Active Directory, cloud-based applications, business applications, etc.
Identity Lifecycle Management therefore supports automated provisioning/de-provisioning flows, workflows for access requests and approvals, and access reviews. It is therefore important to ensure IGA systems have the required breadth of connectors and depth of integration. IGA systems must be able to connect with all the types of source systems in an organization, such as cloud-based applications, for example, as well as have the required depth of integration with business applications that have complex business roles authorization models, such as SAP, for example.
Other Identity Lifecycle Management capabilities include data mapping and data integration tools for data from HR and other sources, and automated reconciliation of changes between source and target systems to highlight unauthorized changes.
Automation
Automation of common IGA tasks has always been a priority for organizations to reduce the inaccuracy and administrative inefficiency associated with the manual completion of IGA tasks. Automation helps make IGA operations leaner and achieve lower TCO.
Most IGA tools provide support for automated provisioning and fulfilment leading to basic automation of IGA requirements. Some organizations have advanced requirements for automation such as automated access reviews and event-driven access certifications.
Reasons Why Businesses Should Care About IGA
The proliferation of digital identities, applications, data, security threats and compliance requirements means that IGA has never been more important. IGA is also important for reducing costs and increasing efficiency around identity management.
Why Does It Make Sense to Combine Identity Provisioning and Access Governance?
Most organizations need Identity Provisioning because it is a core IAM requirement that focuses on tasks related to administering access fulfilment and entitlements throughout an identity lifecycle. Access Governance provides tools for the business to manage workflows and access entitlements, run reports, carry out access certification campaigns, and perform SOD checks. Access Governance is becoming increasingly popular with organizations that require better visibility of identity administration and access entitlements across their IT infrastructure.
In the light of the fact that most organizations require Access Governance for security and compliance reasons, we could conclude that most organizations need both Identity Provisioning and Access Governance, and because these two areas are closely related and benefit from sharing a single UI, integrated auditing and reporting, workflows, connectors, and a single Access Intelligence analytics layer, it makes sense for these two areas to be combined in an integrated IGA solution.

There are several adoption patterns in the market where customers' immediate requirements are limited to either Identity Provisioning or Access Governance, and do not demand an IGA solution. However, in most other cases where there is a need for both, IGA products are preferred over provisioning or governance ‘only’ solutions to achieve the desired mix of capabilities. This is generally true for greenfield IAM implementations that have a need for both Identity Provisioning and Access Governance capabilities.
Does IGA Save Money, Time, and Resources?
IGA helps businesses to reduce costs by enabling the automation of access-related tasks. Automation is also key to saving time and resources. By automating access-related processes wherever possible, means that fewer people in the organization will be involved in access-related tasks, and that these tasks will require less time and attention.
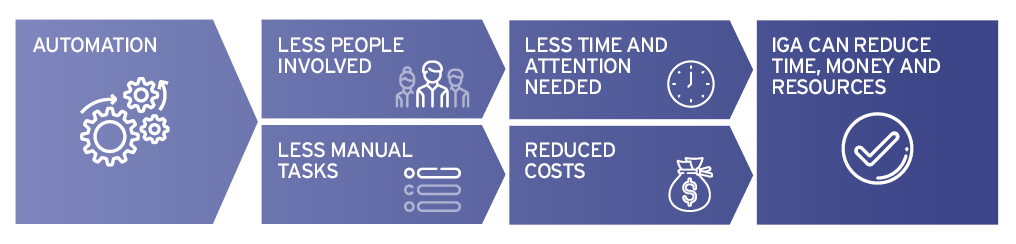
However, organizations must ensure the right mix of manual and automated IGA processes to ensure the effectiveness of processes is preserved by continuously monitoring them against defined key performance indicators (KPIs). While IGA can save money, time, and resources, it is important to approach implementations correctly. Read this Leadership Brief on how to avoid the Typical Risks and Pitfalls for IGA Projects.
Digital identities are at the core of Digital Transformation, Information Security, and Privacy. Therefore, it has never been more important for enterprises to have the capability to manage identities effectively and efficiently. For more information, see this Advisory Note on the Future of Identity Management.
Does IGA Reduce Risks and Increase Security?
IGA is essentially the ability to reduce the risk that comes with excessive or unnecessary user access to applications, systems, and data by enabling policy-based centralized orchestration of user identity management and access control, and working with other IAM processes to automate workflows and meet compliance requirements.
IGA reduces identity-related risks and thereby increases security by enabling better visibility of identity administration and access entitlements across its IT infrastructure. IGA includes machine learning techniques to enable automated access reviews and anomaly detection. By enabling efficient administration of identities and access entitlements, strong role management, and auditing and reporting, IGA helps to reduce much of the security risk associated with identity.
With an IGA solution in place, organizations are much more likely to identify the abuse of stolen credentials by cyber criminals through anomaly detection, and limit lateral movement across IT environments using stolen credentials by enforcing the principle of least privilege.
IGA solutions help to prevent or detect the use of stolen credentials to make unapproved or unauthorized changes, and to prevent fraudulent activities by employees by enforcing separation of duties (SoD) controls. IGA solutions also limit the opportunities for cyber criminals to take advantage of orphan roles and accounts.
The risk around identity is being compounded by the increase in the number of non-human digital identities within organizations, as well as increased access to systems by partners, contractors, and consumers.
IGA products support the consolidation of identity information across multiple repositories and systems of record in an organization’s IT environment. The identity information, including user accounts, associated access entitlements and other identity attributes, are collected from across the connected target systems for correlation and management of individual identities, user groups, and roles through a centralized administration console.
Does It Benefit Compliance?
IGA supports auditing and reporting on access across the IT environment and is therefore a huge help to organizations to prove compliance with the growing number of data regulations around the world, as well as conduct investigations in the event of a data breach.
A detailed audit trail will help investigators to identify accounts associated with the breach and enable them to establish the scope of the breach with accuracy by looking at which systems and data were accessed using the accounts linked to the breach. IGA typically includes identity analytics, which is important for achieving visibility into the operational state of IGA processes by analyzing the operational data generated by IGA tools to evaluate adherence to data protection regulations.
Identity analytics and other tools are often combined in IGA solutions to enable reporting in terms of compliance with major regulatory frameworks.
Most Common Use Cases for IGA
The most common use cases for IGA are those related to reducing costs and increasing security through automation, increased visibility, strictly limited access, and increased efficiency.
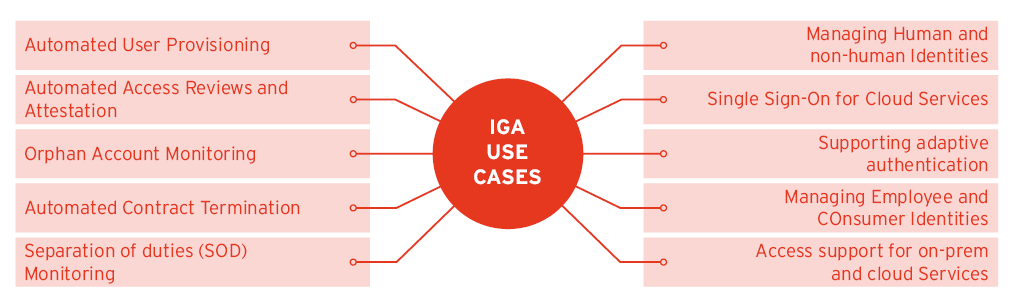
Top IGA Use Cases
Some of the top IGA use cases are listed below. This list is far from exhaustive, but highlights some of the common use cases or goals organizations have in Identity Governance and Administration.
- Automated user provisioning
- Automated access reviews and attestation
- Orphan account monitoring
- Automated contract termination for employees and contractors
- Separation of Duties (SoD) monitoring
- Managing human and non-human identities
- Single sign-on for cloud services
- Supporting adaptive authentication
- Managing employee and consumer identities
- Access support for on-prem and legacy applications as well cloud-based services
This KuppingerCole Buyer’s Guide focusses on IGA solutions. It provides questions to ask vendors, criteria to select your vendor, and requirements for successful deployments.
The Way to Successful IGA Implementation
Most organizations struggle with IGA processes, particularly creating and managing roles, allocating and reviewing access entitlements, and dealing with access requests. The main reason is that organizations are following the wrong approach to IGA.
Policies Are Key
In many cases, IGA is failing to deliver full value to the business because organizations are not approaching it in a way that is aligned with IGA’s principle of policy-based centralized orchestration of user identity management and access control. Many organizations are falling into the trap of starting by defining roles, and then assigning entitlements based on these artificially constructed roles. While this works in theory, in practice this leads only to a minefield of complexity that few organizations can manage.
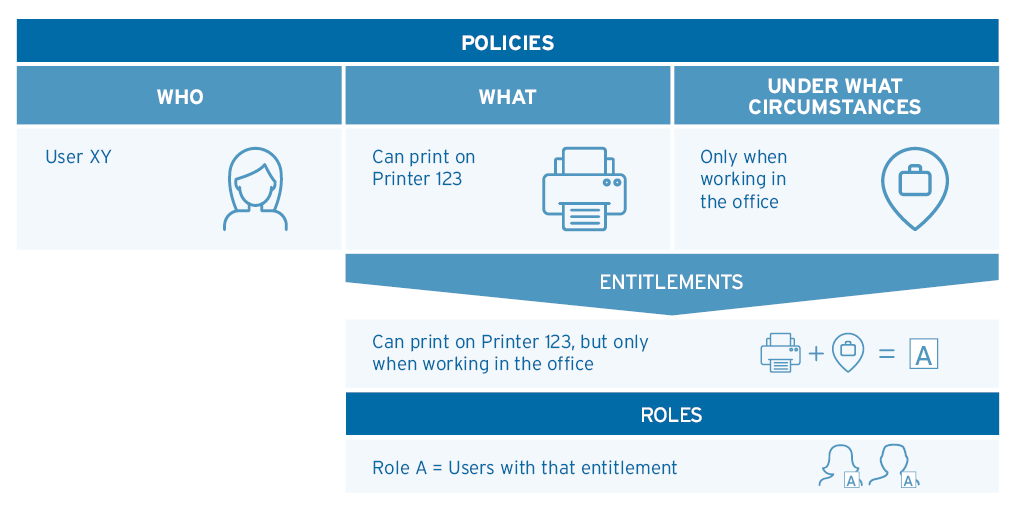
A much better approach is to start with policies. If policies are the foundation of IGA, then it will deliver the business value it is designed to deliver without all the unnecessary complexity associated with the role-based approach. In the context of IGA, a policy is essentially about who has access to what under what circumstances. For example, User A can print on printer 123, but only when working in the office.
The first step, then, is to define policies as described above. Next, group or cluster users with similar entitlements. For example, all those users who can print on printer 123, but only when working in the office. In this way, roles can be derived from the freshly described policies. Finally, permissions or entitlements can be associated with the roles easily because they are already described in the policies. The entitlement in our example policy is “print on printer 123 when working in the office”.
Challenges Around Roles
A policy-based approach has several benefits. First, it avoids creating complex, artificial roles. Second, it starts with policies that everyone can describe easily. Third, if organizations are pragmatic in clustering, they will be able to avoid a proliferation of roles. Fourth, entitlements are easy to define correctly because they are contained in the policies. And fifth, policies can be used to derive other policies such as access management policies and even firewall policies.
Deriving roles from policies also means that organizations can work with a 1-tier model for roles instead of complex multi-tier models that are commonly found in organizations today.
Policies, therefore, are the logical place to start because they contain all the essential elements of access management, which means that everything else can be derived from them. The added benefit of a policy-based approach is that as the technology matures, there will be increasing opportunities to use smart software tools to derive entitlements and even other policies automatically.
Why Automation Is Key to Improved Access Reviews
Automation based on policies is strongly recommended as a way of improving and simplifying access reviews. However, for this to work properly, several important processes need to be in place. First, there needs to be a process for tracking which entitlements have been granted via policies and which have been granted in response to manual requests to ensure that all entitlements are covered either by policy review or individual entitlement review.
Second, there needs to be a process in place for approving policies before they become active. This is to ensure that the translation of policy into concrete entitlements is correct. And third, there needs to be a process for retiring policies when they are no longer appropriate. In theory, if all manual requests can be eliminated and all access entitlements are done automatically based on polices that are well designed, approved, and managed and working correctly, manual access reviews will no longer necessary.
Could Automation Replace Manual Access Reviews?
The fact that policies are already commonly used for things such as Access Management, and the fact that there is no audit standard requesting roles or static entitlements, means that most auditors are used to polices and could well accept the elimination of manual reviews.
The likelihood that auditors will accept that organizations are meeting the requirement of common audit standards is even greater where organizations create, approve, manage, and review policies in structured, well-defined, and well-documented processes. This position can be bolstered even further by adding good processes around identity information quality to ensure the data is always correct.
Although it is unclear how universally the elimination of manual reviews will be accepted by auditors, in the meantime, organizations should aim to achieve as much policy-based automation as possible. This approach will undoubtedly improve the quality of access reviews because there will be far less to do and therefore it will be much easier to do it correctly and efficiently.
While there are other things that can be done to simplify the access review process, such as introducing time-restricted entitlements, policies and automation are the first and most important step towards making IGA simpler as well as more efficient and effective.




































