Among the longstanding challenges that information security leaders have grappled with for years, one stands out: the difficulty of balancing user experience and security. The traditional tug-of-war between ease of access to business-critical applications and resources and robust protection from hackers has never been easy.
Until now.
The unprecedented demands that the COVID-19 pandemic have placed on IT and security teams have tested their flexibility, inventiveness and resolve. But they’ve also had a silver lining. Across industries — particularly in those that are highly regulated or have trended towards early adoption of cloud technologies — interest and investments in Zero Trust security initiatives are at an all-time high.
We surveyed more than 600 security decision-makers across North America, Asia-Pacific (APAC), and Europe, the Middle East and Africa (EMEA) for our recent 2021 State of Zero Trust Security report and discovered that 90% of organisations are currently working on Zero Trust implementation projects or plan to start one in the near future. Despite Zero Trust being coined as a network security concept by Forrester in 2010 (and conceived even earlier by the Jericho Forum), in 2019 only 16% of organisations had begun this journey. In 2020, 41% of organisations were working on Zero Trust initiatives and this shift has accelerated along with the remote working and cloud transformation programmes observed in response to the pandemic. The shift was particularly dramatic in EMEA, where only 18% of organisations had Zero Trust agendas in 2020 and 90% had planned or begun one this year.
For most global organisations, moving from legacy perimeter-based security methodologies (in which internal networks are “trusted” and external ones are “untrusted”) to an identity-centric Zero Trust-based approach (in which identity is the new perimeter and users are secured individually so that they’re able to access the resources they need regardless of the location, device or network from which they’re connecting) isn’t simple or easy.
But pandemic response, combined with the need to support remote work has pushed growing numbers of organisations to accelerate Zero Trust adoption. As they do so, they’re seeing added benefits — enhanced flexibility for users who want to continue working remotely at least some of the time, and less friction for employees who increasingly depend on seamless access to cloud resources if they’re to remain productive in the modern digital business landscape. This trend has the potential to end the battle between usability and security – once and for all.
A key example here is the combined use of Single Sign-On (SSO) and adaptive Multi-Factor Authentication (MFA). SSO enables user access to multiple resources once authenticated. This is convenient for the user but, when used by itself, SSO inherently increases risk as an attacker could likewise use that access if compromised. So, the authentication must be protected with MFA to ensure security.
By making that MFA ‘adaptive’, access can be readily granted to lower risk resources, with unusual or higher risk access attempts prompting a step up authentication challenge. Adaptive, context-based access policies reduce friction for users by prompting for MFA less frequently but ensuring security when it matters.
Identity is the cornerstone of Zero Trust
By definition, Zero Trust is an approach to security that ensures that the right people have the right level of access to the right resources in the right contexts, and that that access is re-assessed continuously — all without adding friction for users. To build a security architecture that achieves this aim, organisations must mature their approach to identity and access management, since identity is the cornerstone of Zero Trust.
As organisations implement Zero Trust architectures, they tend to progress through several relatively consistent stages of maturity.
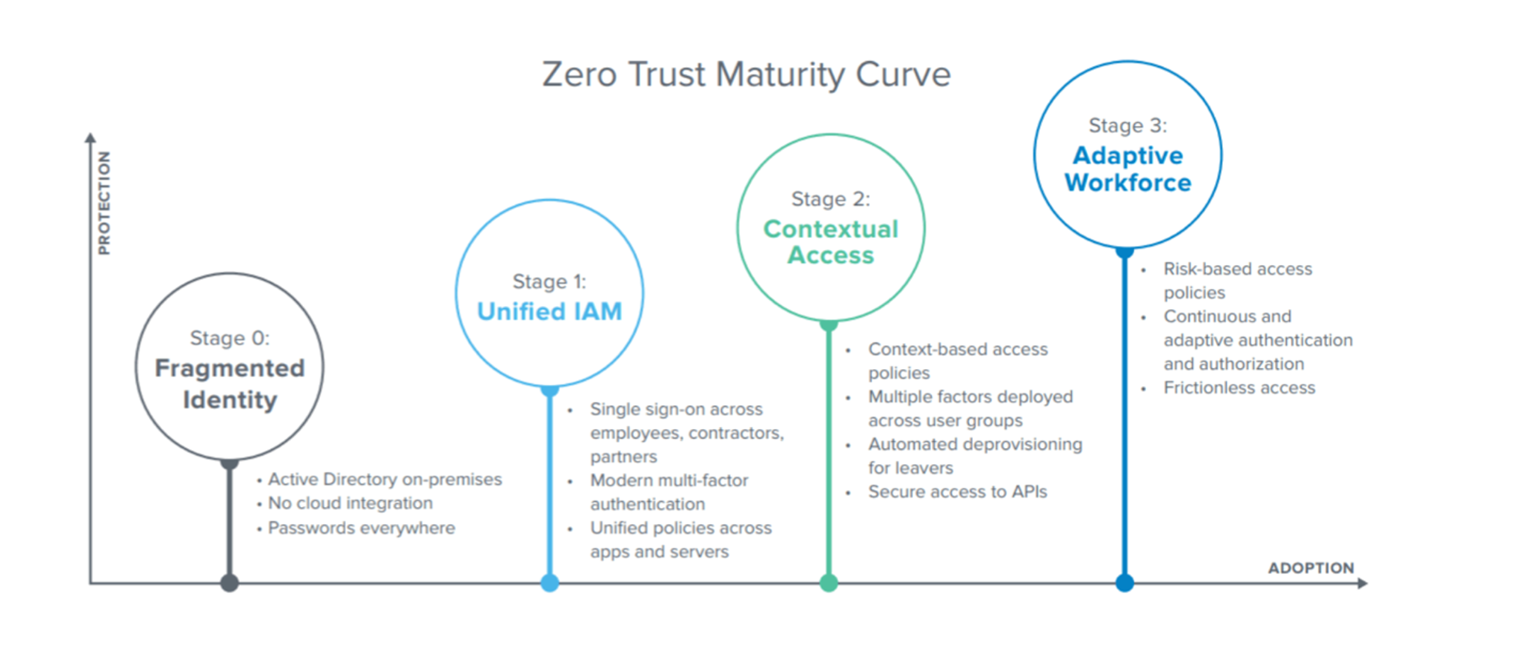
It’s important to note that the technologies adopted by organisations that are further along the Zero Trust maturity curve are those that not only provide more robust and consistent protection for greater numbers of users accessing more and more resources, but also include key capabilities that both simplify management and improve end users’ experience.
Zero Trust is Here to Stay
The shifts that were set in motion by COVID-19 will be with us for the long haul. Even as employees return to the office or work in a hybrid fashion, remote work will remain far more popular and widespread than it was in 2019. And the necessity of having secure and frictionless access to cloud resources as well as a diverse and distributed set of IT assets will only become more foundational for business success. We’ll never go back to yesterday’s perimeter-bound networks.
As a result, it’s a safe bet that adoption of technologies like passwordless and biometric authentication will continue to climb. Passwords are brittle, of course, and maintaining Active Directory on-premises with few cloud integrations creates friction for users and administrative overhead for IT and security teams alike. Modernising with a Zero Trust-based, identity-centric approach creates a win for all stakeholders: the organisation will mitigate today’s greatest risks at the same time that users enjoy seamless experiences and security teams exercise more granular visibility and control. This is why industry analysts, government agencies and regulatory bodies are all increasingly calling for Zero Trust’s large-scale adoption.
To discover more but how Okta’s identity-centric approach to Zero Trust could help your organisation navigate the paradoxical relationship between security and usability click here. Also, don’t forget to register for the KCLive Event Zeroing in on Zero Trust.